For a little less than a year, Silent Circle sells its Blackphone, his famous “anti-NSA” smartphone. Based on Privat OS, an Android derivative, this smartphone has the advantage of being the first secure phone affordable to the general public, with a price of about 630 euros (you have to spend twice more at minimum for the french Bull Hoox for instance). But is it really as secure as the company says?
01net.com got one of those devices from a reseller and we gave it for one week to Sebastian Dudek, a security researcher at Sogeti, an IT services company. He is very fond of connected devices and gave a talk on power line technology last year in November, at NoSuchCon. We asked him: what could a malicious hacker do if he finds (or steals) such a smartphone ?
Within days, the security researcher has identified a major problem: it is possible to dump all the partitions of the Blackphone and to copy them to a computer, without any risk to wipe the data. How is that possible? Actually, the Silent Circle smartphone is identical to a Wiko Wax, itself based on a Nvidia Tegra 4i processor. This type of chipset features a low-level programming mode called APX or nVFlash mode that can be activated by hand. “Just press the power button when the phone is switched off and as soon as the phone vibrates, you have to quickly press the up and down volume buttons at the same time”, explains Sebastian Dudek.
No wipe mecanism
All you have to do then is to install a free software from Nvidia and to connect the device by USB. That’s it. “For a smartphone that aims to be secure, this is one of the first things to defend. Google Nexus models, for example, are equipped with an automatic mechanism that wipes the data when a person tries to activate this type of low-level access”, says Sebastian Dudek. If the user has not activated the Blackphone data encryption, the hacker can immediately catch all the user data, which our security researcher did.
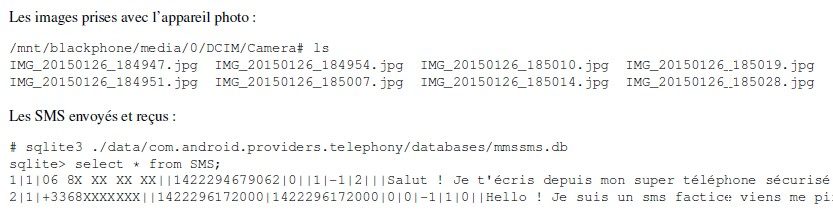
But what if encryption was activated? Are the data totally secured ? Not necessarily. Sure, the partitions copied via APX are encrypted. The encryption key is generated by an algorithm which make use of the password set by the user and some other elements like the masterkey of the device. But the fact is that an attacker can get the hands on those other elements.
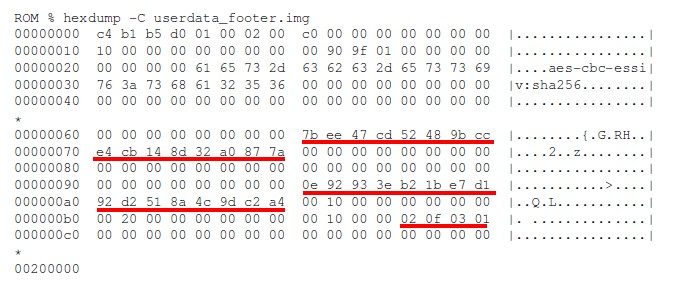
Knowing the algorithm to generate the encryption key (“scrypt” algorithm), our researcher has implemented a brute-force attack on the user’s password in a tool available on Github named “Android fde“. If the password is only four digits long, as it is often the case, the partitions can be decrypted within a few hours. If the password is longer, it depends on the computing power, as well as the victim’s password policy.
Evil Maid attack
Another disturbing detail: the APX mode allows not only to read the partitions of the Blackphone, it also allows you to make changes by using an edit mode. “A person who has physical access to the terminal for a short period of time could, for example, inject malware directly into the boot partition which start the Android system. It is the so called Evil Maid attack scenario”, says Sebastian Dudek. This attack could theoretically be quite powerful. If it is installed in the boot partition, such a malware could control the entire boot process. for instance, it could wait for the moment when the user enters the password and decrypts the phone. And then it could install a second malware directly into the smartphone. However, the researcher did not push his investigation further.
Reached by 01net, Silent Circle did not deny the attack discovered by the security researcher, but wanted to put things into perspective. First of all, the vendor points out that it is a physical attack, which is less harmful than a remote attack. Furthermore, there is a simple way to protect effectively the data by setting a long and complex password. Finally, it should also be noted that the Blackphone make some good points too. The transparent system settings of Privat OS is a good way to limit data leakage. In addition, the device comes with a year’s subscription to silent Circle’s encrypted communications software.
But the most important fact is that the Silent Circle development team is very responsive when there is a security problem. In the past, when a security researcher found a flaw, it was quickly eliminated. It is a pity that this work is marred by the APX vulnerability. The next version of the Blackphone, which was announced in February, will hopefully fix this.
🔴 Pour ne manquer aucune actualité de 01net, suivez-nous sur Google Actualités et WhatsApp.











